About the agent mode
Last updated 2023-06-14
Agent mode is a site-level setting that determines how the Next-Gen WAF agent handles request processing. Options include:
- Blocking: enables request blocking and logging. This option actively protects your web application and provides visibility into your web traffic. Legitimate traffic is still allowed.
- Not Blocking: enables request logging. This option provides visibility into your web traffic but doesn't actively protect your site.
- Off: disables request processing. The agent doesn't block or log requests. This option doesn't uninstall the agent.
About the Blocking option
When the Agent mode menu is set to Blocking, the Next-Gen WAF:
- logs requests based on our storage policy.
- blocks malicious requests from reaching your web servers and doing harm. Site alerts and rules define the criteria used to evaluate and block individual requests.
When requests are blocked, the 406 response code is returned unless you specified a different custom response code. You can view non-sensitive portions of blocked requests and response metadata via the web interface and API.
About the Not Blocking option
When the Agent mode menu is set to Not Blocking, the Next-Gen WAF logs requests based on our storage policy and all traffic is allowed.
IMPORTANT
The Not blocking agent mode never blocks requests. Requests that match rules with a block action will be allowed.
Changing the agent mode
You can change the agent mode for a site via our API and the web interface. To use the web interface to change the agent mode, compete the following steps:
NOTE
Users with an Observer role cannot change the agent mode.
- Log in to the Next-Gen WAF console.
- From the Sites menu, select a site if you have more than one site.
From the site navigation bar, click the agent mode indicator.
Click Manage.
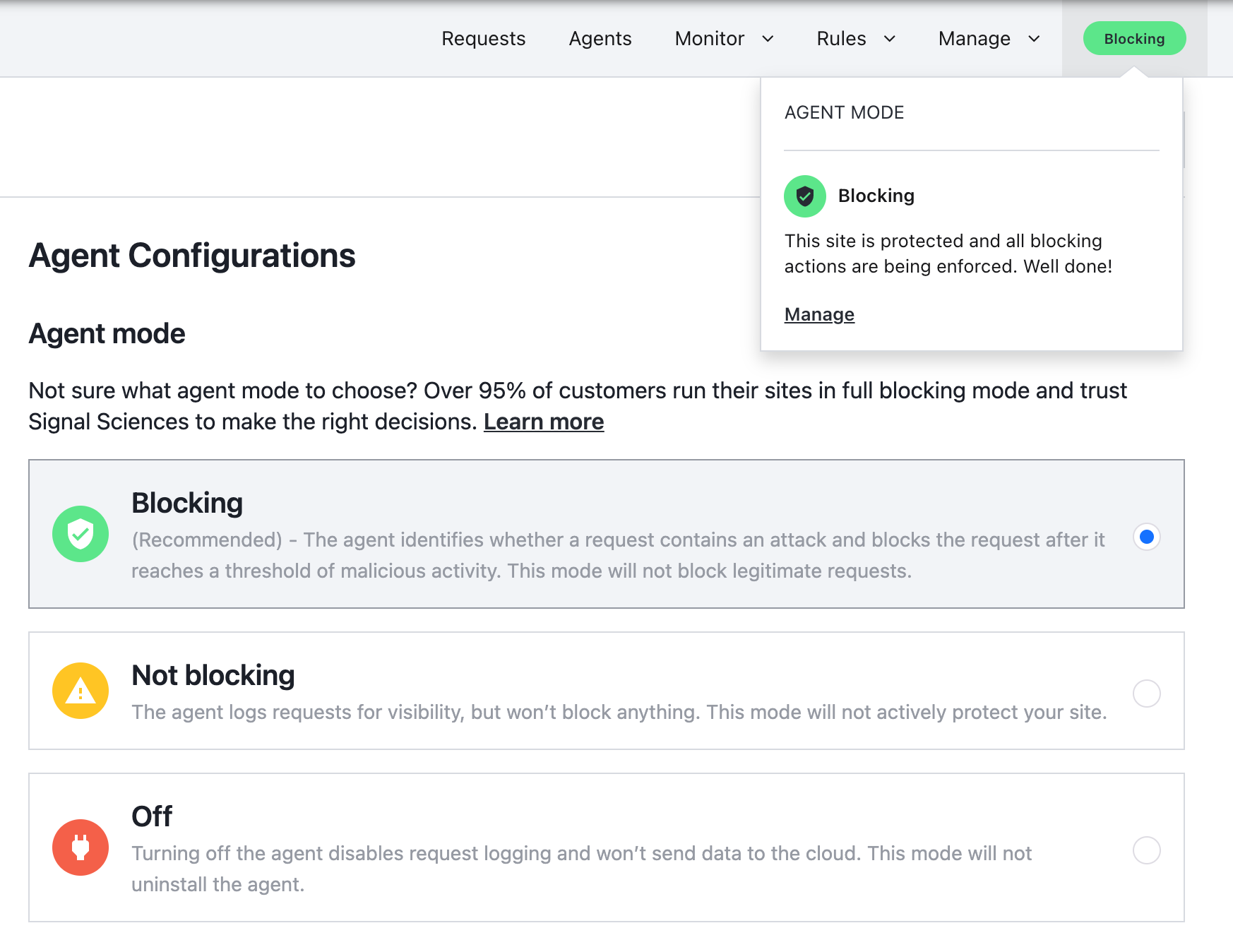
From the Agent mode menu, select the agent mode for the site. Options include:
- Blocking: enables request blocking and logging. This option actively protects your web application and provides visibility into your web traffic. Legitimate traffic is still allowed.
- Not Blocking: enables request logging. This option provides visibility into your web traffic but doesn't actively protect your site.
- Off: disables request processing. The agent doesn't block or log requests. This option doesn't uninstall the agent.
Click Update.
Do not use this form to send sensitive information. If you need assistance, contact support. This form is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.