- English
- 日本語
Setting up TLS with certificates Fastly manages
Last updated 2024-05-14
This guide describes how to use Fastly TLS to enable HTTPS for a domain using a certificate managed by Fastly. To serve secure traffic from Fastly using HTTPS, a website or application needs to provide clients with a valid TLS certificate signed by a trusted certification authority. TLS (Transport Level Security) and its predecessor SSL (Secure Sockets Layer) are the protocols that allow clients to form secure server connections so traffic can be served over HTTPS.
Fastly-managed certificates use the ACME protocol to procure and renew TLS certificates. You have several options for certification authorities:
- Certainly, Fastly's publicly-trusted certification authority
- Let’s Encrypt, a third-party non-profit certification authority
- GlobalSign, a third-party commercial certification authority (only available for paid accounts)
Trial accounts include Fastly-managed certificates for two domains using the Certainly or Let's Encrypt certification authority. Upgrade to a paid account to use GlobalSign or secure additional domains.
TIP
Our TLS subscriptions API allows you to manage Fastly TLS subscriptions programmatically.
Before you begin
Before setting up TLS on your domains, be sure to review the Fastly TLS prerequisites and limitations.
Setting up TLS for a domain
Setting up TLS for a domain requires you to secure the domain by registering it with a certification authority. To start this process through the Fastly control panel (instead of programmatically) follow these steps.
- First-time set up
- Setting up additional domains
To set up TLS for the first time, complete the following:
- Log in to the Fastly control panel and select Security from the navigation sidebar. The Overview page appears displaying an overview of Fastly's security offerings.
- Click Manage certificates.
- Click Get started.
- In the Domain Name field, enter the apex domain (e.g.,
example.com), subdomain (e.g.,www.example.comorapi.example.com), or wildcard domain (e.g.,*.example.com) you want to secure. - From the Certification Authority menu, select one of the certification authorities to secure your certificate. Prices vary between certification authorities, sometimes significantly. Be sure to review the details about these differences on our pricing page.
- From the Select a TLS Configuration menu, select the TLS configuration to apply. The configuration defines both the IPs that the certificate will be deployed to and the associated TLS settings that will be applied. The default option is HTTP/3 & TLS v1.3 +0RTT (t.sni).
- Click Continue. The Domains page appears displaying your domain along with detailed steps on how to verify that you own it.
Verifying domain ownership
To begin serving HTTPS traffic, Fastly needs to verify that you control any domain you’ve added to the control panel. Fastly allows you to verify apex domains and subdomains via the ACME DNS challenge, the ACME HTTP challenge, or via email validation. Each requires you to make specific DNS changes. Wildcard domains require the DNS challenge or email validation challenge type.
IMPORTANT
Fastly may modify the behavior of your services and DNS to complete ACME challenges for domain verification.
- ACME DNS challenge
- ACME HTTP challenge
- Email challenge
The default method for verifying you control a domain being added to a Fastly managed TLS certificate uses the ACME DNS challenge type. It’s suitable for all kinds of domains (apex, subdomains, and wildcards). It will only point the _acme-challenge subdomain at Fastly, allowing you to set up TLS first, before pointing production traffic at Fastly.
To use this verification method, create a CNAME record with a unique target for your domain. Follow the steps below to view the formats for the CNAME record and target.
- Log in to the Fastly control panel.
Go to Security > TLS management > Subscriptions.
Click View subscription details for the subscription you want to make changes to.
Click Verification options in the Verification column for the domain you want to verify. The Verify domain ownership page appears with formats for the record and target.
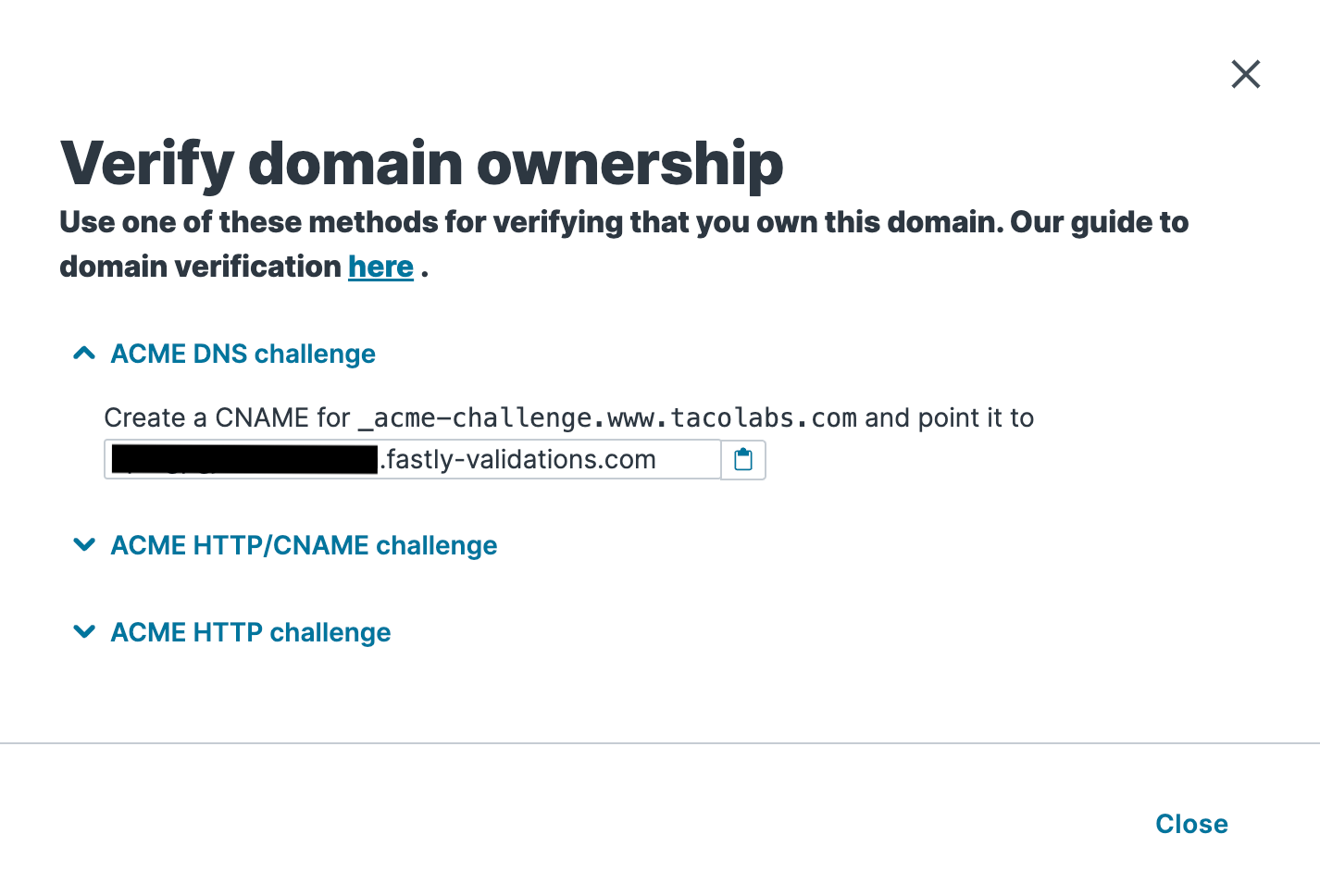
The steps to create the CNAME record will vary depending on your DNS provider's control panel interfaces. Refer to your DNS provider's documentation for exact instructions on how to do this. Your CNAME record must use the format _acme-challenge.DOMAIN_NAME (e.g., _acme-challenge.www.example.com) and must be pointed to a unique target for your domain (e.g., domain_token.fastly-validations.com). Once you’ve pointed your DNS records at Fastly, we encourage you to keep the _acme-challenge subdomain CNAME in place to avoid interruptions in service.
What happens next
It should take no more than an hour for the TLS enablement process to progress through all of the TLS statuses shown below:
| TLS Status | Description |
|---|---|
| Checking domain DNS records… Step 1 of 3 | Domain validation is in progress. Fastly is checking domain DNS records to verify that you control the domain being added to a certificate. To advance to the next enablement state, you must verify control of the domain by updating that domain’s DNS records to complete one of the ACME challenge types. |
| Certificate requested. Waiting for response from CA… Step 2 of 3 | Domain validation has been confirmed. Fastly has verified you control the domain and has requested a TLS certificate for it from the certification authority. |
| TLS enabled (certificate being deployed globally) | The certification authority has issued a TLS certificate. Newly issued certificates can take between 20 minutes to an hour to fully deploy across Fastly’s global network. |
NOTE
If using GlobalSign certificates, after verifying domain ownership you must monitor the DNS resolution process and ensure the domain resolves globally before the TLS certificate will validate and issue. Depending on your DNS vendor, it may take up to 72 hours for your DNS to resolve.
Troubleshooting
If more than an hour has passed and TLS enablement appears to be stalled in one of the stages of adding a domain, there is likely an issue.
Domains stuck in the Checking domain DNS records state
If the domain is stuck in the Checking domain DNS records state, it is likely that you have not configured your DNS records correctly in order to verify domain ownership. You can check the DNS records yourself using a dig command in a command line application as follows:
| ACME challenge type | Command to type |
|---|---|
| HTTP | dig www.example.com +short |
| DNS | dig _acme-challenge.www.example.com +short |
Be sure to replace example.com with the hostname you used when you configured your DNS records.
If you have correctly configured your DNS records, the result from this command will include one of the CNAME or A Records required for verification as defined in the Verifying domain ownership instructions.
If you recently added or modified DNS records, you may need to wait up to 72 hours for your DNS changes to propagate across the internet. If you don’t see these addresses within that time period, you may have misconfigured your DNS records.
If you are still having issues, there may be a Certification Authority Authorization (CAA) record on your domain that is blocking the certification authority from issuing certificates. This CAA record is used to specify which certification authorities (CAs) are allowed to issue certificates for a domain. If a CAA record exists, you may need to correct or remove this record in order to use a managed Fastly TLS certificate.
The following lists the CAA record value needed for each certification authority supported by Fastly TLS:
| Certification authority | CAA record value |
|---|---|
| Certainly | certainly.com |
| Let's Encrypt | letsencrypt.org |
| GlobalSign | globalsign.com |
Domains stuck in the Certificate requested state
If the domain is stuck in the Waiting for a response from CA state, this is likely a temporary issue with the certification authority. Be sure to allow up to an hour in this state before contacting support for assistance. If this is a new certificate request, you can also try deleting the domain and starting again.
TLS activated but certificate not deployed everywhere
If the domain displays the Activated state but the certificate doesn’t appear to be available everywhere, the certificate is likely still in the process of being deployed throughout the Fastly network. It can take anywhere from 20 minutes to an hour for certificates to fully deploy. Be sure to allow up to an hour in this state before contacting support for assistance.
Subscriptions listed as failed
A subscription displays the Failed state if it is a new subscription and fails to issue a certificate for seven days or an existing subscription that fails to renew a certificate for seven days beyond its expiration date. You will also receive an email notification about failed subscriptions.
Subscriptions typically fail if you are not pointing traffic to Fastly or if you don't have proper DNS records in place. GlobalSign subscriptions specifically may fail if the domain hasn't resolved globally, meaning it's not accessible from anywhere in the world. Use a tool like DNS Checker to ensure your domain is propagated globally.
Once you resolve these issues, you can try to re-issue the subscription using the steps below:
- Log in to the Fastly control panel.
- Go to Security > TLS management > Subscriptions.
- Click View subscription details for the failed subscription.
- Click Retry now.
After you retry a failed subscription, we will try to issue or renew the associated certificate for a 24-hour period. If we still cannot obtain a certificate after 24 hours, the subscription will again be marked as failed.
Pointing DNS to serve HTTPS traffic
To serve secure traffic via HTTPS once the certificate is deployed, follow these steps.
Ensure that the domains you've added via the TLS domains interface have been added to a properly configured Fastly service.
Configure your DNS records to point traffic at the newly created certificate’s IP addresses. If you used the HTTP challenge method to verify domain ownership, you’re already pointing traffic at the certificate. All DNS details (CNAME, A records, and optionally AAAA records) can be found by clicking See DNS details to view the TLS configuration associated with the domain.
For an apex domain (e.g.,
example.com), you'll need to create an A record with your DNS provider. For subdomains and wildcard domains (e.g,www.example.comor*.example.com), you'll need to create a relevant CNAME record.
Your domains and certificates can be set to use one or more TLS configurations. For more information, refer to the details on managing DNS and TLS configurations.
WARNING
If you point your DNS away from Fastly after the initial setup, we will be unable to terminate TLS on your behalf and we will also be unable to renew your certificate, which will expire after 90 days.
Managing TLS subscriptions
You can use the Subscriptions page to manage your TLS subscriptions and take actions such as:
- adding or removing domains
- changing the domain common name
- migrating to Certainly, Fastly's certification authority
- deactivating TLS
Managing domains on TLS subscriptions
To manage the domains on your TLS subscriptions, such as to add or remove domains or to change the domain common name, follow these steps:
- Log in to the Fastly control panel.
Go to Security > TLS management > Subscriptions.
Click View subscription details for the subscription you want to make changes to.
Click Manage Subscription.
NOTE
You can only manage a subscription in
Pending,Issued, andRenewingstates.From the Manage Subscription details page, you can do the following:
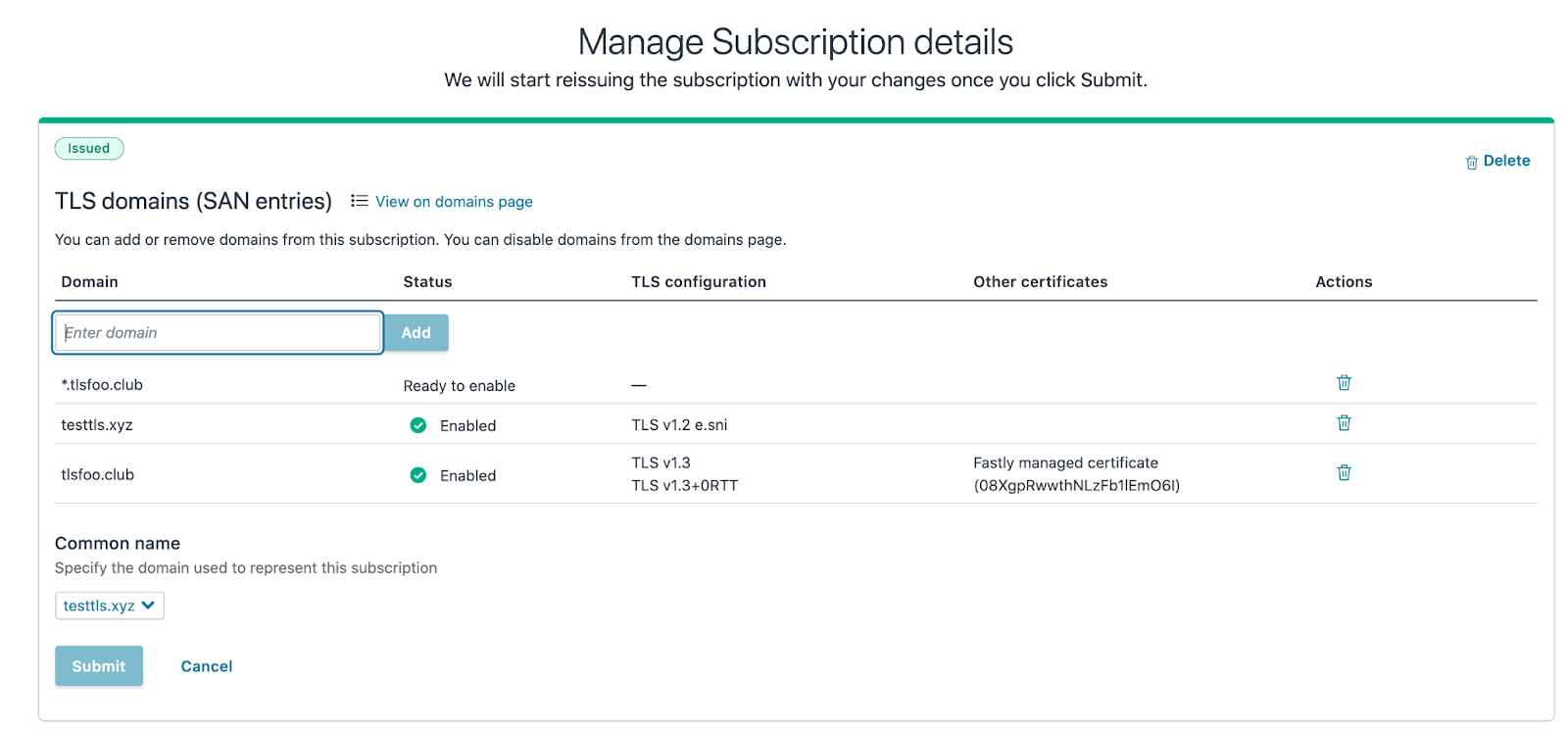
- Add new domains: In the Domain field, enter one or more apex domains (e.g.,
example.com), subdomains (e.g.,www.example.comorapi.example.com), or a wildcard domain (e.g.,*.example.com) and click Add. Separate multiple domains with a comma. - Remove existing domains: Click the trash
 in the Actions column on the same line as the domain you want to delete. Follow the instructions in the confirmation window to complete the deletion.
in the Actions column on the same line as the domain you want to delete. Follow the instructions in the confirmation window to complete the deletion. - Change the subscription common name: From the Common name menu, select the domain used to represent this subscription.
- Add new domains: In the Domain field, enter one or more apex domains (e.g.,
After making any changes to the subscription, click Submit. A message appears asking to confirm your changes.
Click Confirm changes to submit your changes. To return to the previous screen, click No, review changes.
NOTE
If you added a new domain, you must validate domain ownership after confirming the change. See Domain validation for TLS certificates.
Migrating to Certainly
If you're using the Let’s Encrypt or GlobalSign certification authorities to secure your domains, you can use the Fastly control panel to migrate to Certainly, Fastly's publicly-trusted certification authority.
NOTE
To migrate from GlobalSign to Certainly, first contact Fastly Support.
To migrate to Certainly:
- Log in to the Fastly control panel.
Go to Security > TLS management > Subscriptions.
Click View subscription details for the subscription you want to make changes to.
Click Migrate to Certainly.

Confirm that you want to migrate your certificate, then click Migrate to Certainly.
After clicking migrate, Fastly will automatically replace your certificate with a Certainly certificate and verify domain ownership without any downtime. Fastly will continue to serve your existing certificate until it is replaced by Certainly. If there were changes to your DNS records that prohibit Certainly from validating your domain and Fastly can't automatically verify the ownership, a notice will appear with instructions you'll need to make to your DNS details.
Deactivating TLS and deleting a TLS domain
Once a domain has TLS activated, you have the option to deactivate TLS via the Deactivate TLS button listed on each domain card on the TLS domains page. If a domain has multiple certificates, you can elect to deactivate a specific certificate by clicking Add/Edit Activations and clicking the Deactivate button next to any active configurations. If all certificates are deactivated, Fastly will no longer serve TLS traffic on the selected domain and it will become disabled. Fastly will attempt to renew a certificate for a disabled domain. To prevent this renewal process, delete the associated subscription after you disable it. Fastly will not renew certificates for deleted subscriptions.
Certificate management and renewals
Each certification authority has a separate verification and renewal time frame that Fastly follows when managing your certificates:
Certainly renewals. Certainly issues certificates that are valid for 30 days. Fastly will attempt to re-verify your domain and renew your certificate after 20 days. However, if your DNS records no longer point at Fastly or if a CAA record blocks Certainly, the certificate will lapse at the end of the 30-day period.
Let's Encrypt renewals. Let’s Encrypt issues certificates that are valid for 90 days. Fastly will attempt to re-verify your domain and renew your certificate after 60 days. However, if DNS records no longer point at Fastly or if a CAA record blocks Let's Encrypt, the certificate will lapse at the end of the 90-day period.
GlobalSign renewals. GlobalSign issues certificates that are valid for 365 days. Fastly will attempt to re-verify your domain and renew your certificate after 275 days. However, if DNS records no longer point at Fastly, or if a CAA record blocks GlobalSign, the certificate will lapse at the end of the 365-day period. Certificates provided by GlobalSign are subject to the terms of GlobalSign's Subscriber Agreement, which can be found at https://www.globalsign.com/repository.
Fastly automatically runs a DNS check for certificate renewals within the following timeframes:
- Certainly: 10 days before certificates are due to expire
- Let's Encrypt: 30 days before certificates are due to expire
- GlobalSign: 90 to 120 days before certificates are due to expire
If a DNS check indicates that a renewal is failing, Fastly will automatically email all account users with TLS management permissions, notifying them of the upcoming expiration. If the renewal continues to fail, Fastly will continue to email users on the account on a schedule up until the expiry date.
In addition, you must verify domain ownership as part of the management process. If you have the correct DNS records for verifying domain ownership and there is no blocking CAA record, but you are still receiving renewal failure emails, contact support for assistance.
Do not use this form to send sensitive information. If you need assistance, contact support. This form is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.