X-SigSci-* request headers
Last updated 2024-12-02
X-SigSci-* headers are added to incoming requests. The end user (your customers) can't see them. However, your internal application can use these headers for various integrations.
NOTE
If you are using the module-agent deployment method, your deployment module may alter the case of header names (e.g., X-SigSci-AgentResponse may appear as X-Sigsci-Agentresponse).
Headers that are automatically added
The Next-Gen WAF automatically adds the following X-SigSci- headers to requests:
| Header | Description | Deployment type |
|---|---|---|
X-SigSci-AgentResponse | A code that indicates the Next-Gen WAF agent's decision to allow or block a request to your web application. The 200 agent response code indicates the request should be allowed, and agent response codes greater than or equal to 301 indicate the request should be blocked. | Core WAF |
X-SigSci-EdgeModule | The VCL version of your Edge WAF deployment and if the VCL is enabled for dynamic backends (e.g., vcl 2.7.0;backendtoken). | Edge WAF |
X-SigSci-RequestID | A request ID used to uniquely identify a request. Not all requests will be assigned an ID. | All |
X-SigSci-Tags | A CSV string of comma-separated signals that are associated with a request. The header includes both system and custom signals (e.g., SQLI, XSS, NOUA, TOR, SITE.CUSTOM-SIGNAL). | All |
X-SigSci-Decision-MS | The time the WAF takes to enrich a request with headers and potentially block it. This header can only be used in VCL. | Edge WAF |
Adding headers to customize inspection for Edge WAF deployments
If you have an Edge WAF deployment, you can use X-SigSci-* headers to customize when the Next-Gen WAF inspects traffic.
Forcing inspection
When testing your Next-Gen WAF deployment, you can use the curl command line tool to force the Next-Gen WAF to inspect a request by adding the x-sigsci-force-inspection header to the request:
$ curl ${REQUEST_URL} -H 'x-sigsci-force-inspection: true'Disabling inspection
The x-sigsci-no-inspection header prevents the Next-Gen WAF from inspecting requests that meet user-defined conditions. For example, you can use this header to bypass the WAF and allow traffic to access static content.
To disable inspection for select requests, add the x-sigsci-no-inspection header to your service and then associate a condition to the header:
- Log in to the Fastly control panel.
- From the Home page, select the appropriate service. You can use the search box to search by ID, name, or domain.
- Click Edit configuration and then select the option to clone the active version.
- Click Content.
In the Headers area, click Create a header.
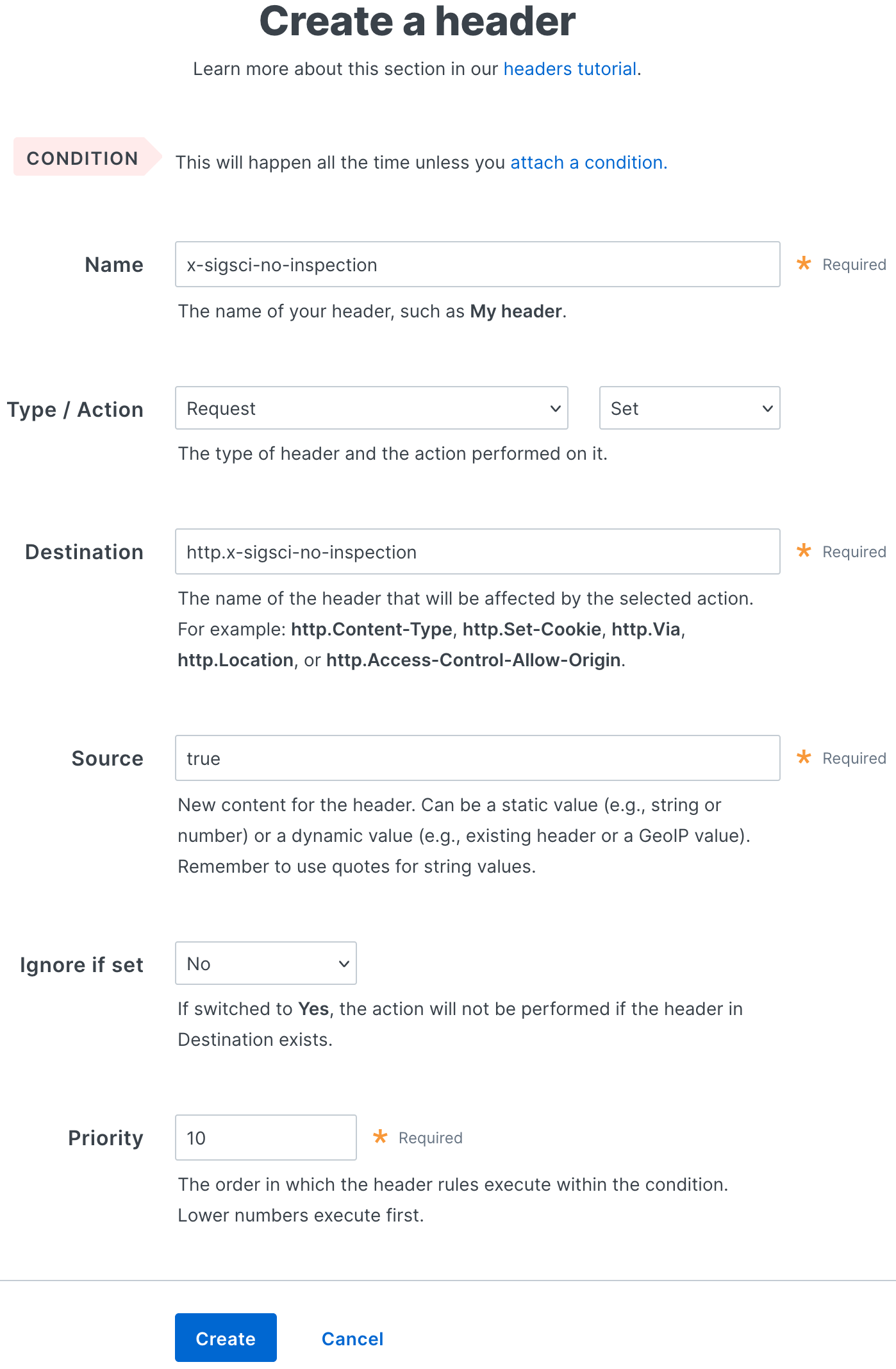
Fill out the Create a header fields as follows:
- In the Name field, enter
x-sigsci-no-inspection. - From the Type menu, select Request, and from the Action menu, select Set.
- In the Destination field, enter
http.x-sigsci-no-inspection. - In the Source field, enter
true. - From the Ignore if set menu, select No.
- In the Priority field, enter the order the header rules execute.
- In the Name field, enter
Click Create.
In the Headers area, click Attach a condition next to the
x-sigsci-no-inspectionheader.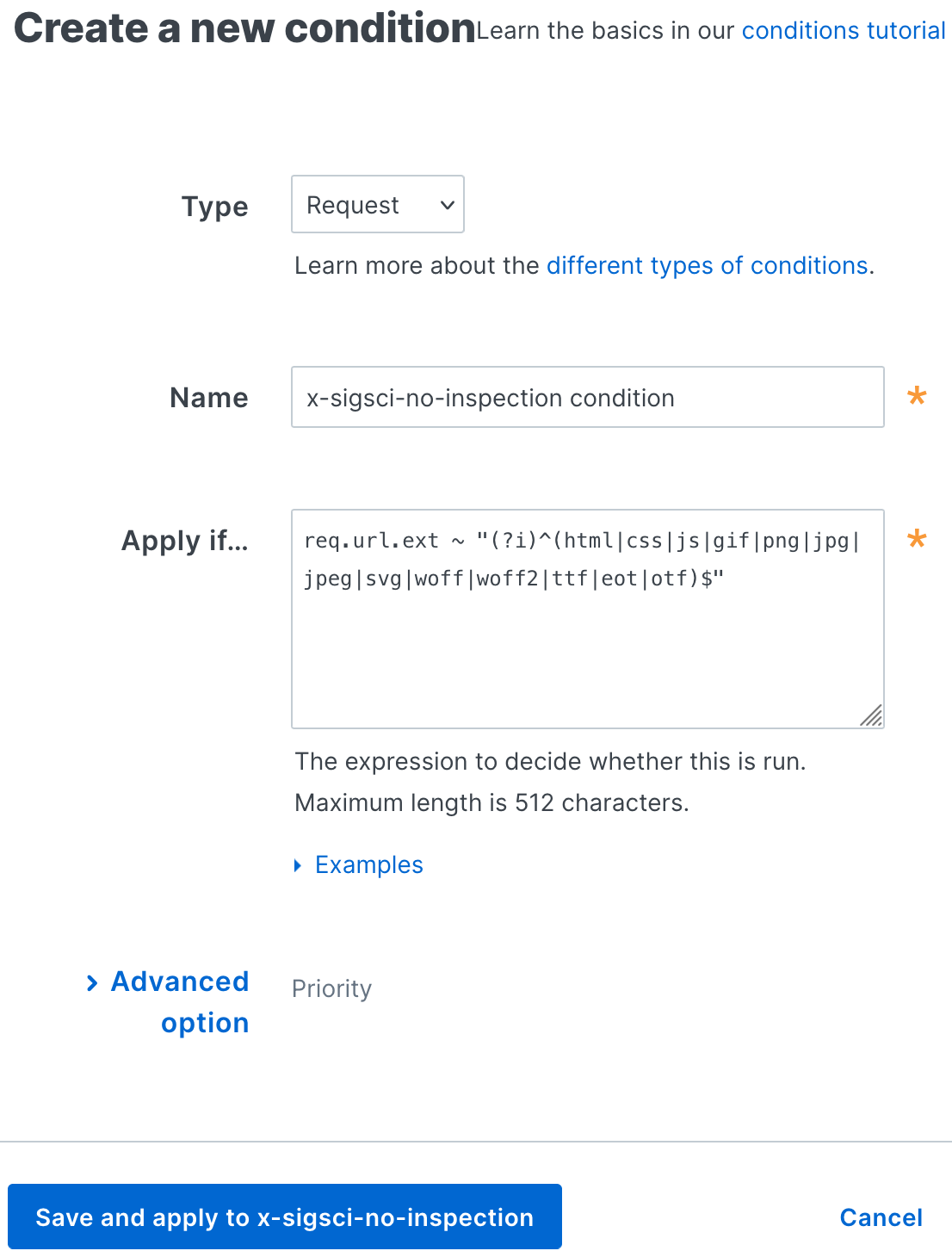
Fill out the Create a new response condition fields as follows:
- In the Name field, enter a descriptive name for the new condition (for example,
x-sigsci-no-inspection condition). - In the Apply if field, enter the appropriate request condition that will be applied. For example,
req.url.ext ~ "(?i)^(html|css|js|gif|png|jpg|jpeg|svg|woff|woff2|ttf|eot|otf)$"disables inspection for requests with a static file extension.
- In the Name field, enter a descriptive name for the new condition (for example,
Click Save and apply to. The new condition for the header is created.
- Click Activate to deploy your configuration changes.
Skipping initial inspection
The x-sigsci-skip-inspection-once header tells the Next-Gen WAF to skip initial inspection and only inspect requests when the vcl_miss or vcl_pass subroutines are called. Adding this header is helpful when you want an additional security integration to handle preflight requests and then the Next-Gen WAF to inspect the request.
To skip initial inspection, add the x-sigsci-skip-inspection-once header to your service and then associate a condition to the header:
- Log in to the Fastly control panel.
- From the Home page, select the appropriate service. You can use the search box to search by ID, name, or domain.
- Click Edit configuration and then select the option to clone the active version.
- Click Content.
In the Headers area, click Create a header.
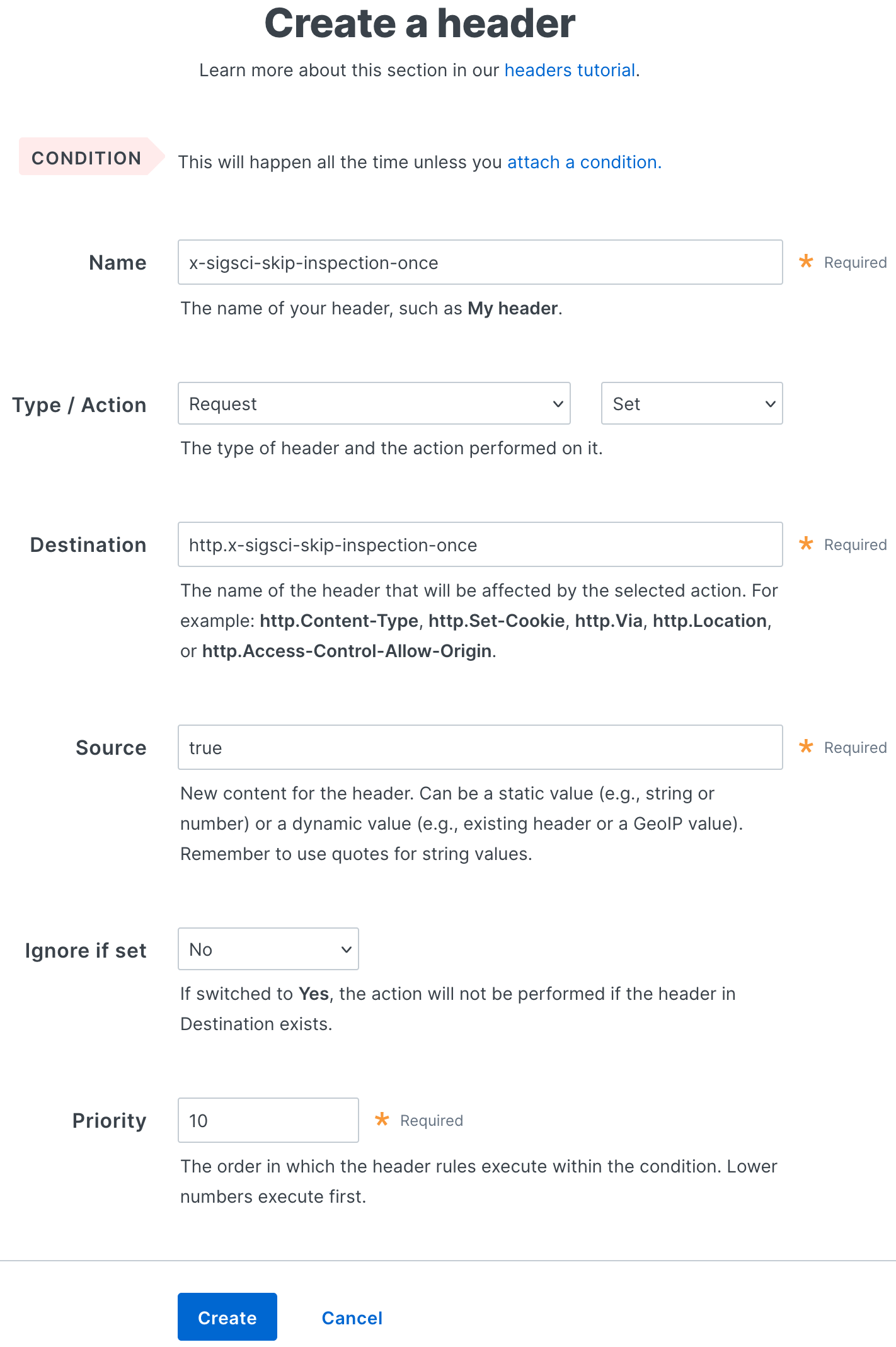
Fill out the Create a header fields as follows:
- In the Name field, enter
x-sigsci-skip-inspection-once. - From the Type menu, select Request, and from the Action menu, select Set.
- In the Destination field, enter
http.x-sigsci-skip-inspection-once. - In the Source field, enter
true. - From the Ignore if set menu, select No.
- In the Priority field, enter the order the header rules execute.
- In the Name field, enter
Click Create.
In the Headers area, click Attach a condition next to the
x-sigsci-skip-inspection-onceheader.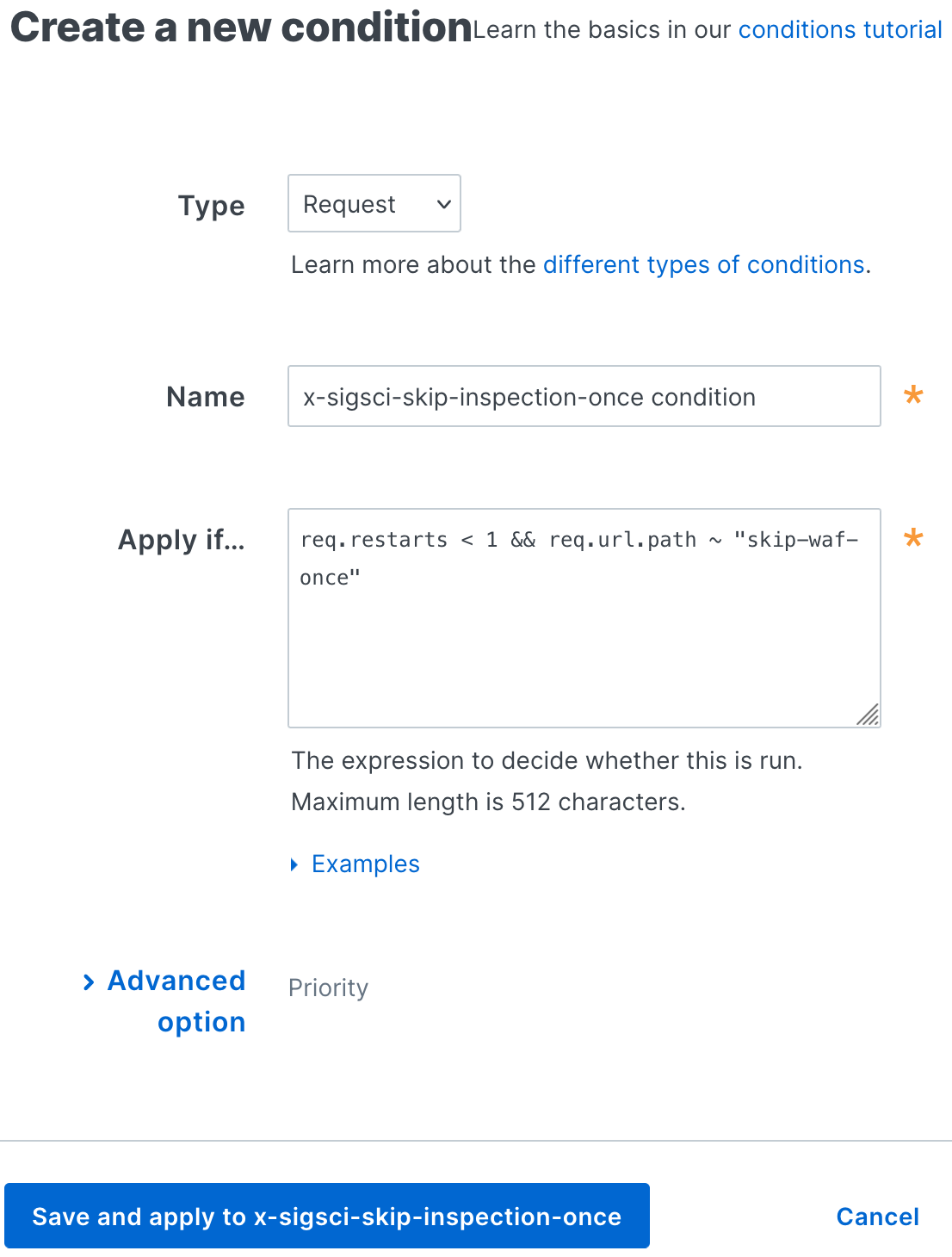
Fill out the Create a new response condition fields as follows:
- In the Name field, enter a descriptive name for the new condition (for example,
x-sigsci-skip-inspection-once condition). - In the Apply if field, enter the appropriate request condition that will be applied. For example, enter
req.restarts < 1 && req.url.path ~ "skip-waf-once"to restart inspection of requests with theskip-waf-oncepath. The restart condition enables preflight requests to enrich a request before being sent to the Next-Gen WAF and origin.
- In the Name field, enter a descriptive name for the new condition (for example,
Click Save and apply to. The new condition for the header is created.
- Click Activate to deploy your configuration changes.
Do not use this form to send sensitive information. If you need assistance, contact support. This form is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.