Edge WAF deployment using the Fastly control panel
Last updated 2025-04-10
IMPORTANT
This guide only applies to customers with access to the Next-Gen WAF product in the Fastly control panel. If you have access to the Next-Gen WAF control panel, check out our Setting up Edge WAF deployments using the Next-Gen WAF control panel guide.
The Edge WAF deployment method hosts the Next-Gen WAF on Fastly’s Edge Cloud platform via our global network of POPs, integrates with Fastly’s caching layer, and is managed by Fastly. Since security processing happens at the edge, the Next-Gen WAF can inspect all traffic before it enters your origin infrastructure and block attacks close to where they originated. You do not need to make any modifications to your own hosting environment.
Prerequisites
Before setting up an Edge WAF deployment, be sure you have the necessary prerequisites in place.
Limitations and considerations
When enabling the Next-Gen WAF for your CDN services, keep the following in mind:
- Enabling, disabling, or making changes to Fastly Next-Gen WAF on a service immediately impacts all service versions, including the active one.
- Access to the Next-Gen WAF in the Fastly control panel is only included for customers on the Essential platform who don't have access to the Next-Gen WAF control panel. All other Next-Gen WAF customers can access the product through the Next-Gen WAF control panel.
- Edge WAF deployment using the Fastly control panel is only supported for CDN services. To use Edge WAF deployment with Compute services, use the Next-Gen WAF control panel instead.
- Edge WAF deployment is not compatible with CDN services that use mutual TLS to the origin.
- Adding the Next-Gen WAF to an existing CDN service counts against the service chain limit.
- A CDN service can be linked to a maximum of one workspace. A workspace can be linked to multiple CDN services.
- Only users assigned the superuser role can enable and configure the Edge WAF deployment for CDN services.
Setting up the deployment
To deploy the Next-Gen WAF on an existing CDN service, complete the following steps:
- Fastly control panel
- Fastly Security API
- Log in to the Fastly control panel.
- From the Home page, select the appropriate service. You can use the search box to search by ID, name, or domain.
- Click Edit configuration and then select the option to clone the active version.
Click Security.
In the Next-Gen WAF card, click the pencil
 to edit the following deployment settings and then click Submit:
to edit the following deployment settings and then click Submit: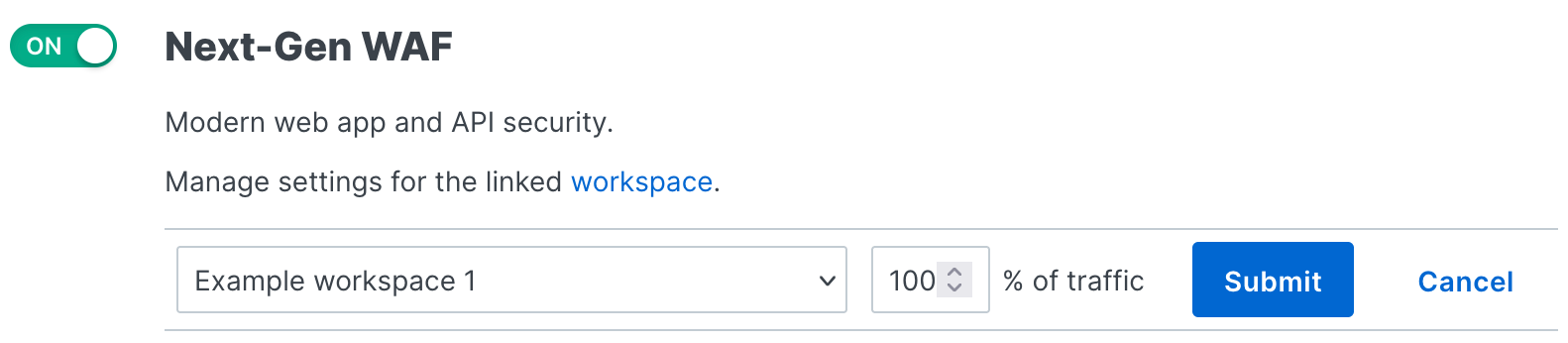
- From the Workspace menu, select the workspace that you want to link to the service. If your account only has one workspace, this field is read-only.
- In the % of traffic field, enter the percentage of traffic that you want the Next-Gen WAF to inspect. When set to
100, all traffic to your service is inspected. When the value is less than 100, a random sample of the specified percentage is inspected.
Click the switch to the On position.
(Optional) Use attack tooling to verify that the Next-Gen WAF is monitoring your web application and identifying malicious and anomalous requests.
Configuring the deployment
To update your deployment, complete the following steps:
- Fastly control panel
- Fastly Security API
- Log in to the Fastly control panel.
- From the Home page, select the appropriate service. You can use the search box to search by ID, name, or domain.
- Click Edit configuration and then select the option to clone the active version.
Click Security.
In the Next-Gen WAF card, set the switch to the On position to enable the Next-Gen WAF for your service or to the Off position to disable the Next-Gen WAF for your service.
If the Next-Gen WAF is enabled, click the pencil
 to edit the following deployment settings and then click Submit:
to edit the following deployment settings and then click Submit:
- From the Workspace menu, select the workspace that you want to link to the service. If your account only has one workspace, this field is read-only.
- In the % of traffic field, enter the percent of traffic that you want the Next-Gen WAF to inspect. When set to
100, all traffic to your service is inspected. When the value is less than 100, a random sample of the specified percentage is inspected.
(Optional) Use attack tooling to verify that the Next-Gen WAF is monitoring your web application and identifying malicious and anomalous requests.
Disabling the deployment
To disable Edge deployment for your service, complete the following steps.
- Fastly control panel
- Fastly Security API
- Log in to the Fastly control panel.
- From the Home page, select the appropriate service. You can use the search box to search by ID, name, or domain.
- Click Edit configuration and then select the option to clone the active version.
- Click Security.
- In the Next-Gen WAF card, click the switch to the Off position.
Using headers to customize inspection
You can use X-SigSci- headers to force the Next-Gen WAF to inspect requests, to disable inspection, and to skip initial inspection.
Do not use this form to send sensitive information. If you need assistance, contact support. This form is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.